Sensitive Content Classification
Protect your company’s most sensitive content with AI data classification.
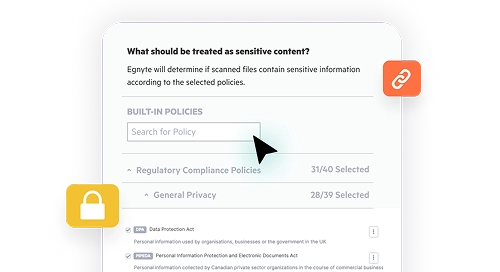
Classify Your Sensitive Content
Identify sensitive content and eliminate the need for disparate data classification tools.
Focus on Your Most Sensitive Data
Review sensitive content from a single, convenient location.
Reduce Exposure
Take immediate action to protect sensitive information that’s exposed.
Streamline Compliance
Comply with wide-ranging data privacy and cybersecurity regulations.
Sensitive Data Discovery Software Features
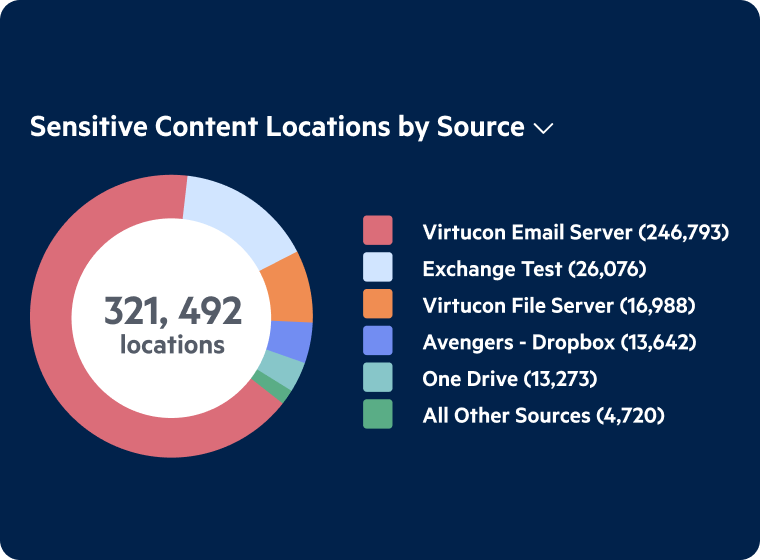
Sensitive Content Dashboard
- See where your sensitive content resides across all data repositories
- Assess the risk level of highly sensitive content
- Take immediate action to protect exposed data
- Align dashboard review with your organization’s most critical compliance requirements
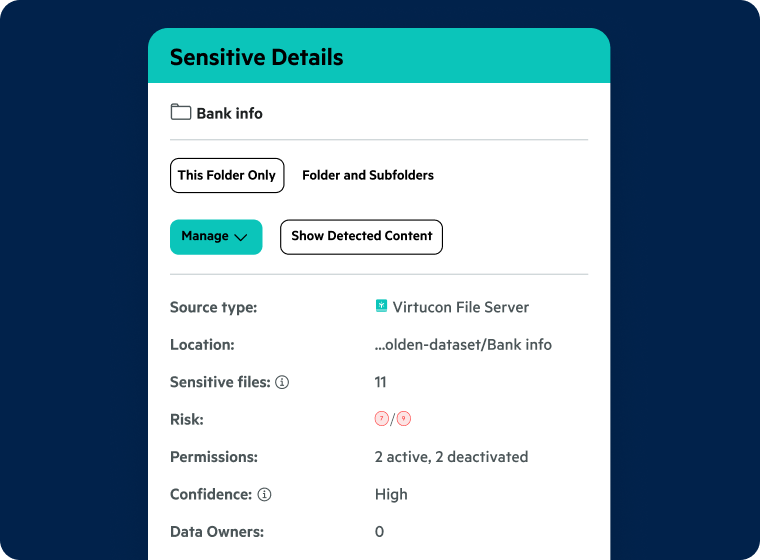
Sensitive Content Details
- Assess the number of sensitive files in folders and subfolders
- Prioritize protection of your highest-risk content with a convenient risk score for sensitive files
- Determine which cybersecurity or data privacy regulations apply to folders or individual files
- Assess which groups and users can access ultra-sensitive content
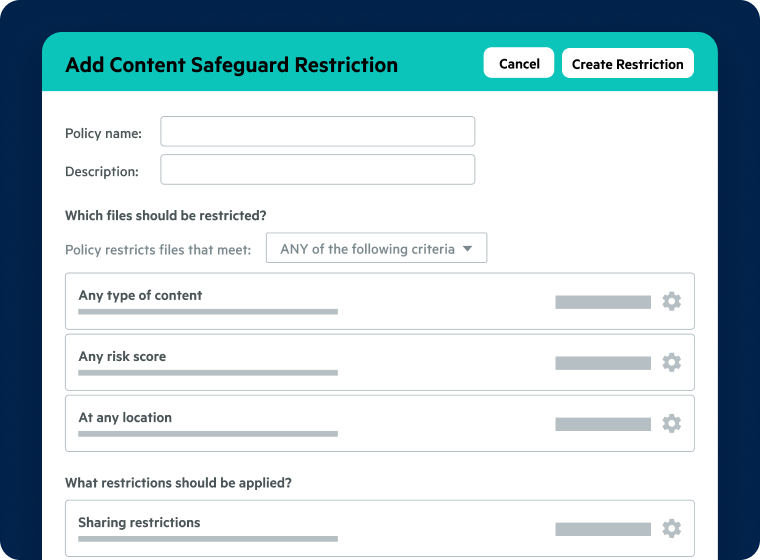
Content Safeguard Policies
- Enforce data-sharing policies based on content type, risk score, and location
- Implement meaningful policy-based content restrictions in minutes
- Allow users to share only the content they have access to
- Create exceptions for groups or user types based on your business requirements
Privacy and Compliance Monitoring
- Identify sensitive content that’s subject to cybersecurity and data privacy regulations such as PCI-DSS, GDPR, CPRA, and SOX
- Reduce manual workloads with automated labeling of sensitive data
- Focus your attention on content with the highest exposure risk
- Implement content classification policies that align with your company’s business requirements
Hear From Our Customers
See Egnyte’s Sensitive Content Classification in Action
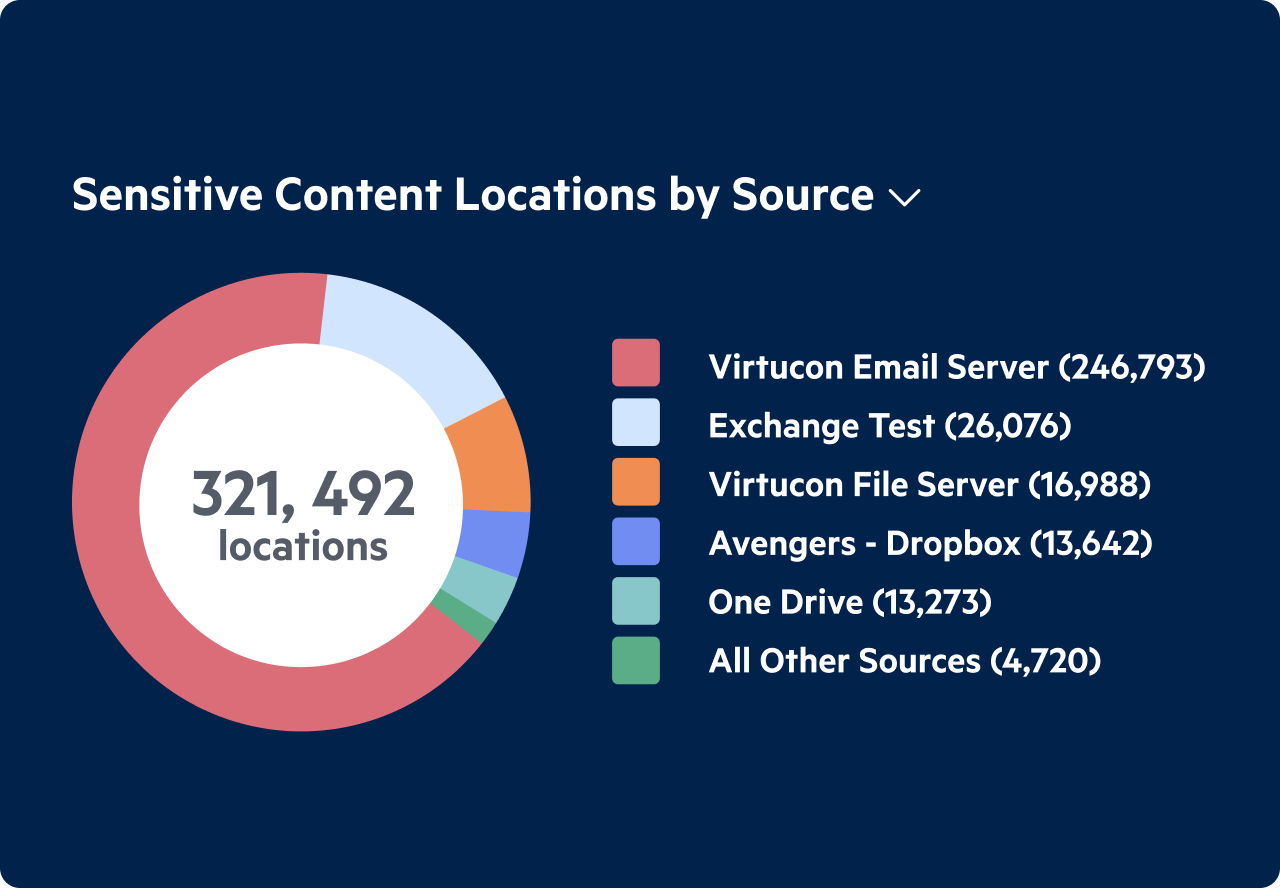
Improve regulatory compliance and protect mission-critical content by:
- Identifying sensitive content across your IT environment
- Taking immediate action to protect exposed content
- Implementing content safeguard policies to improve security protection



